-

Custom software development services from MetaSys
DATE:According to a survey, 8 out of 10 customers consider the experience a company offers to be equally significant as the products or services it provides. Source: “State of Service,” Salesforce, December 2020. Customer service is no longer an afterthought; it’s a core competency. Companies that do a great job of providing excellent customer service …
Custom software development services from MetaSys Read More »
-

Tips to Prevent WordPress Website Hack
DATE:WordPress is a well-known open-source PHP based CMS (Content Management System) platform used for writing blogs and developing websites. Easy accessibility of WordPress leads to a variety of threats and malware attacks. WordPress security is the highest priority for any organization that has a website. In addition, Google’s rule on blacklisting all websites with malware …
-
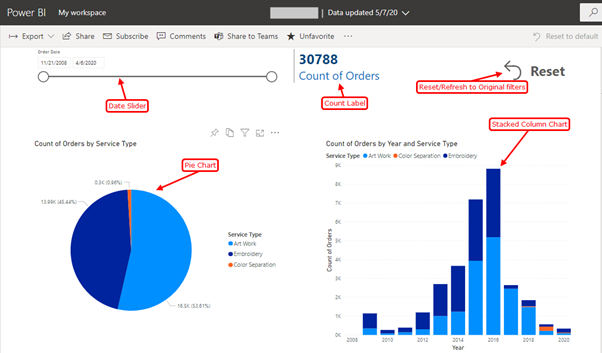
Power BI – A Visualization Tool which is easy to understand and develop
DATE:Power BI is a tool used for generating business intelligence reports, charts and graphs, that incorporate easy to understand visuals. It is a self-service BI tool that is particularly useful for data analysts who create and distribute BI reports throughout the organization. With moderate knowledge of SQL, one can develop simple power BI visuals after …
Power BI – A Visualization Tool which is easy to understand and develop Read More »
-

Few tips to help you get better at building app features through Unit Testing
DATE:At MetaSys, we place great importance on writing unit tests, as it leads to faster development and reduces the time it takes for software to get to the production stage.Unit testing is the first step of software testing, where individual units/components of a software are verified. A unit refers to the smallest module of any …
Few tips to help you get better at building app features through Unit Testing Read More »
-

Barcode Scanning for a web based application
DATE:In this article I will share some information about a recent barcode scanning implementation we did for a web based application for one of our clients. Barcodes are nothing more than a machine readable form of data represented in the form of lines. Nowadays, barcodes are an essential part of inventory management for a number …
-

Web API security using JSON web tokens
DATE:Today data security during financial transactions is super important and critical. The protection of sensitive user data should be a major priority for developers working on applications that use financial or personal information of the clients. These days, many apps are accessed through multiple devices including desktops, laptops, mobile phones and tablets. Both web apps, …